Jade Unified Security Framework (USF)
 The Jade Unified Security Framework (USF) is a thin extendable security layer that operates across machines in a network. It provides hooks for applications and security components to register and effect network wide security changes. The USF protects specific protocols and services using components both in user and kernel spaces. The USF is a working functional prototype which has been protecting our networks for the past few years. It was designed as an easy to deploy solution for Small to Medium Enterprises (SMEs) without the need for expensive security hardware. The design is highly modular with USF utilities and analyzers being easy to maintain and build upon.
The Jade Unified Security Framework (USF) is a thin extendable security layer that operates across machines in a network. It provides hooks for applications and security components to register and effect network wide security changes. The USF protects specific protocols and services using components both in user and kernel spaces. The USF is a working functional prototype which has been protecting our networks for the past few years. It was designed as an easy to deploy solution for Small to Medium Enterprises (SMEs) without the need for expensive security hardware. The design is highly modular with USF utilities and analyzers being easy to maintain and build upon.
Four functional USF components or groups work together to detect, analyse, and react to protect a network. They are the core firewall, system and network logging (SIEM), application layer defenses, and other threat specific countermeasures.
Core Firewall Components
 The core firewall is made up of iptables/ipset firewall configurations running on our main firewall/router and protected server machines. Real time lower layer threat detection and responses are provided by functions in the firewall. Network logging actively correlates threats, detects issues, and supports off-server analysis over extended periods. It enables long-term detection beyond the capabilities of internal state-based tools. The main firewall/router machine processes all traffic before forwarding it to the internal network. This machine actively detects threats for itself and internal machines. Internal machines with simpler server configurations conserve resources and skip blocklist processing.
The core firewall is made up of iptables/ipset firewall configurations running on our main firewall/router and protected server machines. Real time lower layer threat detection and responses are provided by functions in the firewall. Network logging actively correlates threats, detects issues, and supports off-server analysis over extended periods. It enables long-term detection beyond the capabilities of internal state-based tools. The main firewall/router machine processes all traffic before forwarding it to the internal network. This machine actively detects threats for itself and internal machines. Internal machines with simpler server configurations conserve resources and skip blocklist processing.
 The firewall iptables solution implements a limited stateful firewall but with the addition of ipset based blocklist processing. Ipset databases contain blocking data based on protocol, IP address, IP network ranges (networks) and time to live (TTL) data. These blocks reside in the Linux kernel making access time fast and efficient while at the same time removing the need to embed blocklist data within firewall configurations.
The firewall iptables solution implements a limited stateful firewall but with the addition of ipset based blocklist processing. Ipset databases contain blocking data based on protocol, IP address, IP network ranges (networks) and time to live (TTL) data. These blocks reside in the Linux kernel making access time fast and efficient while at the same time removing the need to embed blocklist data within firewall configurations.
Blocks are either time based (will timeout on their own inside the kernel) or permanent. External systems maintain ipset databases outside the firewall and update them based on directives from other USF components. Most blocks begin as limited-time restrictions and automatically expire. If future detections identify the same threats from the same source, a progressive backoff algorithm extends the duration of the new block. If a threat persists beyond a critical threshold, the system marks it as permanent and updates the firewall to reflect this status.
SIEM: Security Information and Event Management
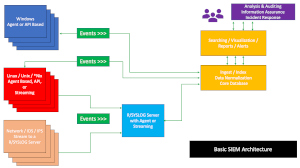 Security Information and Event Management (SIEM) is a security solution that collects, analyzes, and correlates data from various sources within an organization’s IT environment to detect and respond to potential security threats in real-time. The Jade USF centralized log server collects and consolidates system logging information from machines on the network.
Security Information and Event Management (SIEM) is a security solution that collects, analyzes, and correlates data from various sources within an organization’s IT environment to detect and respond to potential security threats in real-time. The Jade USF centralized log server collects and consolidates system logging information from machines on the network.
The logging server collects, categorizes and stores received incidents. Standalone analyzers provide operator status updates (via email) and often interact with the underlying network firewall to effect near real-time network blocks of ongoing attacks. The modular analysis and reporting tools are based on easy to write and adjust scripts. Currently existing reporting tools mainly focus on email and authentication related attacks. These tools can be easily modified and applied to any detected threat type. Existing tools regularly check for various authentication attacks (ssh, sip, smtp, imap, http) and automatically block detected threats within the network firewall. Additional tools check for application specific attacks, in particular in support of our various WordPress installations.
SIEM plugin tools enable custom analysis deployment based on incident types. They analyze application incidents, such as authentication attacks across sessions, which the application logs but cannot detect or act upon. The specific plugin tool determines whether changes to the USF are permanent or time-based.
Application Service Security

Application protocols under active monitoring include HTTP (web), SMTP (email MTA), SSH (secure shell access), IMAP (email remote message store access), SIP/RTP/IAX (VoIP), and others. The system actively detects and responds to security incidents across multiple layers:
- with the service application itself (postfix, apache, imapd, sshd, etc)
- application logging to the SIEM server
- within the network stack itself (firewall configuration)
 Threats are often detected by different tools requiring different processing. In the case of email MTA’s, the postfix service detects and acts on repeated authentication attacks within a single session. Postfix is unable however to detect these attacks across sessions. SIEM intelligent threat analysis plugins have the ability to correlate new threats with historical data. This allows for the implementation of progressive backoff algorithms and variable time to live blocking within the USF firewalls.
Threats are often detected by different tools requiring different processing. In the case of email MTA’s, the postfix service detects and acts on repeated authentication attacks within a single session. Postfix is unable however to detect these attacks across sessions. SIEM intelligent threat analysis plugins have the ability to correlate new threats with historical data. This allows for the implementation of progressive backoff algorithms and variable time to live blocking within the USF firewalls.
In specific cases, iptables actively detects application layer attacks at the network layer. For example, with SSH secure remote access, the system identifies and blocks repeated failures within a short time window at the IP layer. The current USF firewall executes this process on every machine in the network. However, similar to the email example, the system retains attack history for only a limited time, making this just the first defense layer. The network stack (Linux kernel) also logs SSH attacks to the SIEM server for extended retention and analysis.
Authentication Attacks
 The most common application layer threats we see are authentication attacks. These happen when remote attackers try to login to a service to gain access to resources. Repetitive dictionary style attacks from a single source trying to guess login credentials is one common example. Today these often take the form of a distributed attack coming from many simultaneous remote IP addresses. Often rather than being continuous they break off an attack only to come back later to resume. They happen at both the protocol level and application layer, such as web based login attempts. The most common protocols we see attacked are SSH and SIP however attacks against email protocols such as SMTP and IMAP continue to rise.
The most common application layer threats we see are authentication attacks. These happen when remote attackers try to login to a service to gain access to resources. Repetitive dictionary style attacks from a single source trying to guess login credentials is one common example. Today these often take the form of a distributed attack coming from many simultaneous remote IP addresses. Often rather than being continuous they break off an attack only to come back later to resume. They happen at both the protocol level and application layer, such as web based login attempts. The most common protocols we see attacked are SSH and SIP however attacks against email protocols such as SMTP and IMAP continue to rise.

As noted earlier, the firewall actively mitigates some attacks in real-time. It does this for both SSH and SIP attacks within a single session. Likewise, the Postfix MTA actively detects and deflects authentication attacks during a single session. In both cases, the system logs incidents to the SIEM server. Custom SIEM analysis scripts identify all other authentication attacks, including multi-session SSH, SIP, and SMTP attacks, as well as other protocols like IMAP and HTTP (web application). USF utilities then handle detected threats by adding the attacking host using the appropriate USF firewall blocking script.
SPAM Prevention
 Unsolicited Commercial E-Mail (UCE), otherwise known as SPAM has been a costly problem for email users for a long time. Common forms include solicitations for buying products or services. Often these messages are phishing attempts to get users to reveal sensitive information and result in identity theft, and many times result in significant financial loss for users unaware of the criminal intent. Some contain dangerous payloads that can infect the computer or device of the recipient.
Unsolicited Commercial E-Mail (UCE), otherwise known as SPAM has been a costly problem for email users for a long time. Common forms include solicitations for buying products or services. Often these messages are phishing attempts to get users to reveal sensitive information and result in identity theft, and many times result in significant financial loss for users unaware of the criminal intent. Some contain dangerous payloads that can infect the computer or device of the recipient.
We have a zero tolerance policy towards spam received (or sent) from our systems. Our team confirms spam received through our monitored accounts and feeds it into our SPAMPROC system. This system actively analyzes message headers to identify the IP address of the submitting mail host. It then promptly updates our DNS Blocklist (DNSBL) to include the confirmed spam relay host, enabling our MTAs to block new messages from that route instantly. The system automatically generates a report in standard ARF format and sends it to the domain administrator listed in the relevant WHOIS record, allowing them to take appropriate action.
Web Services
 Jade Networks hosts numerous virtual websites, primarily using WordPress and RoundCube, but also supports other platforms, especially Docker container-based ones. For WordPress installations, we recommend one of several popular web application firewalls (WordPress plugins). We tested multiple Apache security modules, but their added overhead, and in some cases thermal overhead, proved excessive.
Jade Networks hosts numerous virtual websites, primarily using WordPress and RoundCube, but also supports other platforms, especially Docker container-based ones. For WordPress installations, we recommend one of several popular web application firewalls (WordPress plugins). We tested multiple Apache security modules, but their added overhead, and in some cases thermal overhead, proved excessive.
All web environments produce their own SIEM logging. WordPress configurations categorize and log data separately, refining the type of analysis required. SIEM analyzers then check each of these separately for context specific threats and act accordingly.
Other Countermeasures
Security solutions like pfSense, OPNsense, and the USF serve as essential tools but cannot replace robust operating system hardening, effective system administration, and thorough network monitoring. Over the years, we extensively tuned and tested kernel parameters (sysctl) related to network resources. We standardized these changes across our network and integrated them into every server. Simultaneously, we implemented proper thermal management, particularly for our Ryzen-based systems, through BIOS adjustments and developed user-level checks and controls under Linux. These efforts eliminated the thermal runaway issues we previously encountered.
Network monitoring is also very important. We used Zabbix in the past with very good results. It integrates SNMP based checks and monitoring with custom checks and notification scripts. The excellent visual representation of network and server health greatly assists in the administration of the network and is easy to integrate with USF tools.